Dissecting WannaCry
WannaCry is by far the most severe malware attack so far in 2017, and the spread of this troubling ransomware is far from over.
WannaCry – How it works…
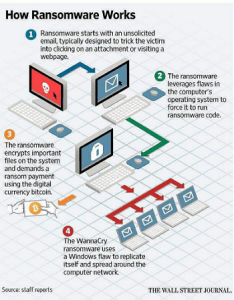
Attack Extent

Why was the attack so successful?
- Cyber security awareness is very low. When attacked, the course of action is not known resulting in unchecked spread of the malware
- Until now, ransomware was regarded as a relatively rudimentary threat. It is usually spread through emails that are sent en masse to target unwary individuals. Attacks against organizations and businesses have been far lesser in number and impact. Until NOW!. Big organizations usually have sophisticated detection methods to prevent and contain infections. The version of WannaCry that spread so rapidly on Friday is different, however: its designers have supercharged it by using tools leaked by the most powerful cyber arsenal in the world — that owned by the US National Security Agency.
- It spread without exploiting user interactions – the EternalBlue exploit works over the Internet without requiring any user interaction. Since it strikes over networks, it can still wreak havoc inside a local network even with the killswitch active, as the killswitch needs the internet to work
- WannaCry exploits WINDOWS vulnerability (Windows 7 and XP in particular). WINDOWS is the most widely used OS across the globe as depicted below:
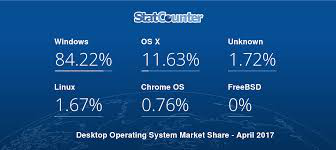
- Microsoft had released a patch to remove the vulnerability in March 2017. But apparently were not installed as needed.
- The reported incidents are far fewer than the actual numbers. A greater percent of the organizations and individuals use pirated version of the OS and attacks on such systems go unnoticed. India is the world’s third largest user of unlicensed software, especially Windows. A report by Kaspersky Lab, which was confirmed by a cyber-security analyst from Gartner, suggests that India is the third-largest source of WannaCry ransomware attacks.
The Future…
New variants of WannaCry have already been detected and many new variants can emerge
Prevention
- Use only genuine products – OS, anti-virus software
- Keep your system always updated. Any patch recommended by the providers needs to be installed automatically
- Take periodic and systematic backup of the data
- Be aware of the any suspicious activity in your system and network and take action immediately
- Report the incident to the local authorities to aid in malware containment if possible
References:
https://www.ft.com/content/af74e3f4-373d-11e7-99bd-13beb0903fa3
https://securelist.com/blog/research/78411/wannacry-faq-what-you-need-to-know-today/
http://www.popsci.com/time-to-start-thinking-about-how-to-survive-next-ransomware-attack
ABOUT THE AUTHOR
Madhu S. Sastry
Madhu has been with Mauverick for 5 years. She currently heads the technical documentation vertical.
Madhu has over 12+ years of experience in development and technical writing. She was earlier a part of Accenture and has worked on Unix shell scripting, Core Java and J2EE technologies with domain expertise in telecom and Cyber security.
